CVE-2022-26148 Arbitrary viewing of ZABBIX account password vulnerability in grafana login status or unauthorized access status
2022-2-25 23:53 作者:酷帥王子 | 黑盒网络渗透测试 | 标签: https://tvd.wuthreat.com/#/listDetail?TVD_ID=TVD-2022-05784
Arbitrary viewing of ZABBIX account password vulnerability in grafana login status or unauthorized access status

1、 Vulnerability details
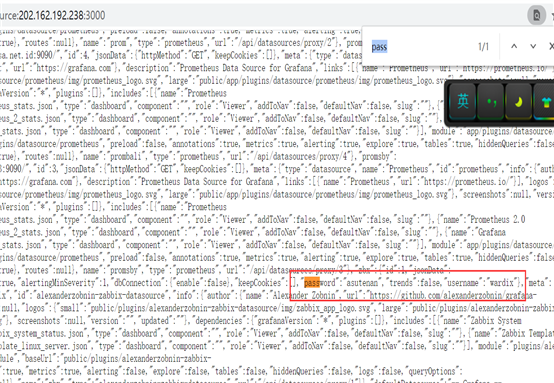
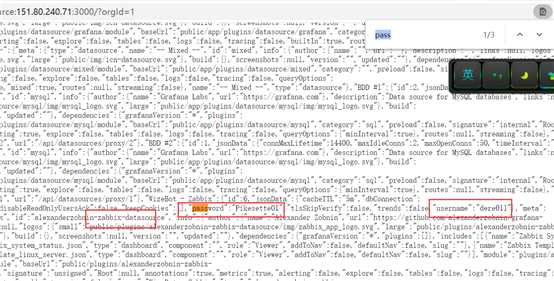
When the user logs in and allows the user to register, right-click to view the source code and Ctrl + F to search for password and api_jsonrpc.php to get the ZABBIX account password and URL address
2、Exploit proof
Case 1:
Case 2:
http://222.209.84.37:3000/login?redirect=%2F
Grafana v4.1.2 (commit: v4.1.2)
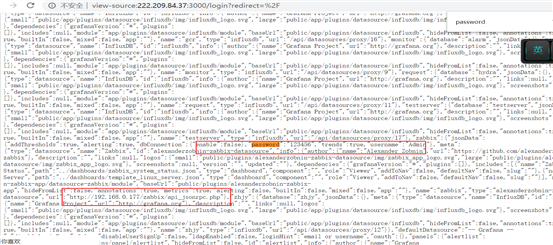
Case 3:
http://42.101.12.205:3000/login
Grafana v5.1.3
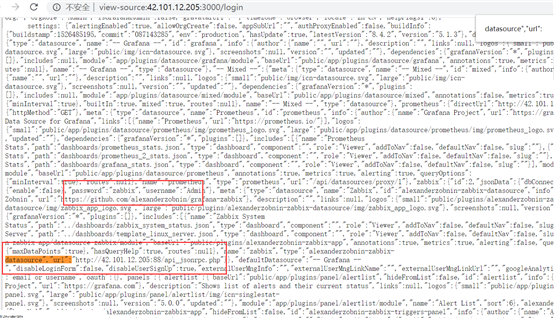
Case 4:
http://42.192.181.95:3000
Grafana v4.1.2
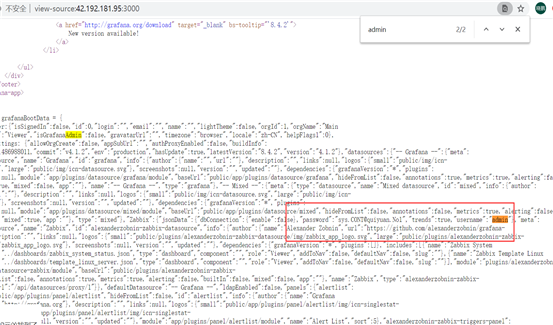
Case 5:
http://59.53.86.104:3000/
Grafana v6.6.2
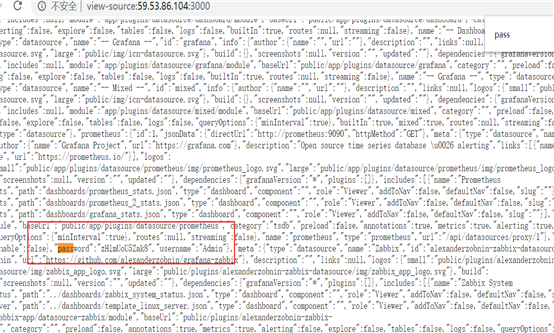
Case 6:
http://202.162.192.238:3000/
Grafana v6.2.3
Case 7:
http://151.80.240.71:3000/?orgId=1
Grafana v7.3.4
3、 Vulnerability hazard
It can cause the URL address of ZABBIX account password to be leaked, so as to use ZABBIX vulnerability bash to rebound the shell
![]() 文章作者:酷帥王子
文章作者:酷帥王子
文章地址:https://www.2k8.org:443/post-319.html
版权所有 © 转载时必须以链接形式注明作者和原始出处!

发表评论: